


Dark Web Monitoring: A Deep Dive into Leaked Credential Monitoring
With the increasing threats in the cyber world, protecting one’s personal information and digital assets has become more critical than ever. The dark web, a hidden part of the internet only accessible using special software, is a breeding ground for illicit...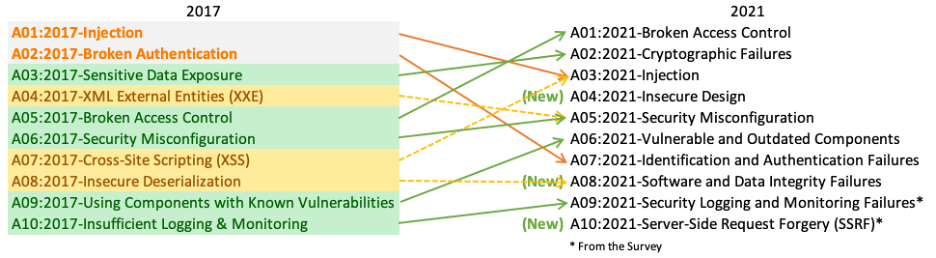
OWASP Top 10
The Open Web Application Security Project (OWASP) is a prominent, non-profit international organization dedicated to enhancing the security of web applications. One of OWASP’s foundational beliefs is in making their resources readily available for free on their website.
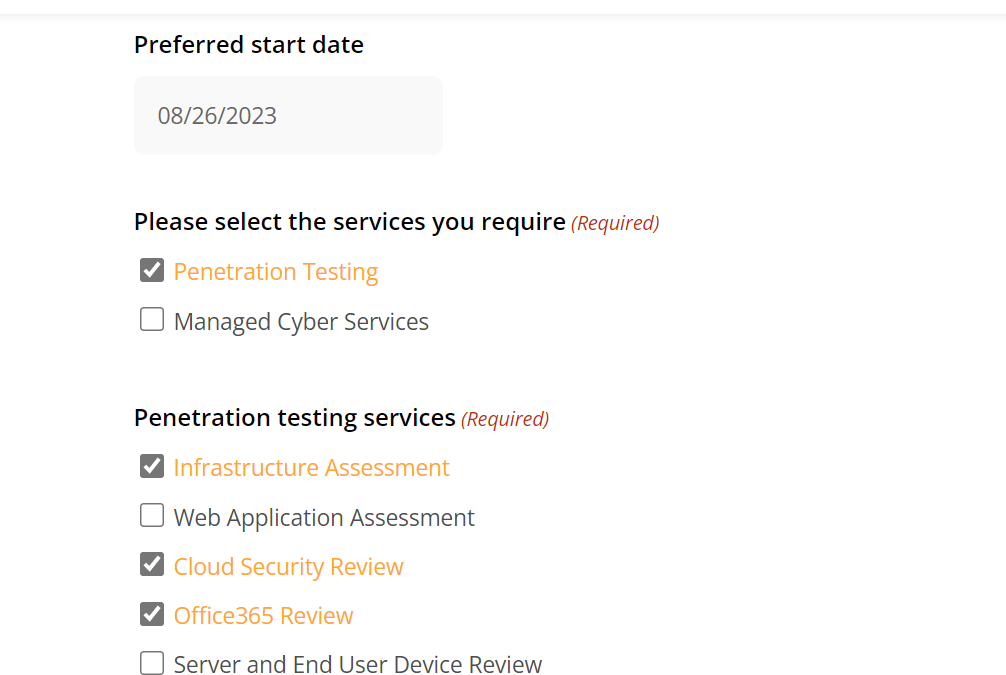
How to Streamline Project Scoping and Enhance Pentest Efficiency
Get quotes instantly and see them right in the scoping form. No need to sign up before getting your quote – we’re all about being upfront and transparent, without any aggressive sales tactics. At Attack Vector, we’ve introduced an innovative...
