Attack Vector Blog Resources Knowledge Repository Research
10 Steps to Cyber Resilience
One of the primary challenges organisations face is ensuring robust cyber security. With cyber threats becoming increasingly intricate and persistent, a proactive and well-informed approach to defense is paramount. The UK's National Cyber Security Centre (NCSC)...
Dark Web Monitoring: A Deep Dive into Leaked Credential Monitoring
With the increasing threats in the cyber world, protecting one's personal information and digital assets has become more critical than ever. The dark web, a hidden part of the internet only accessible using special software, is a breeding ground for illicit...
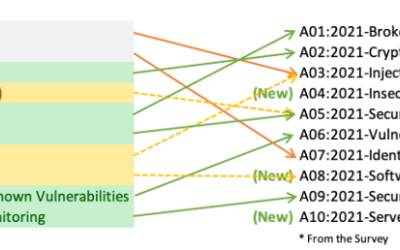
OWASP Top 10
The Open Web Application Security Project (OWASP) is a prominent, non-profit international organization dedicated to enhancing the security of web applications. One of OWASP’s foundational beliefs is in making their resources readily available for free on their website.
How to Streamline Project Scoping and Enhance Pentest Efficiency
Get quotes instantly and see them right in the scoping form. No need to sign up before getting your quote – we're all about being upfront and transparent, without any aggressive sales tactics. At Attack Vector, we've introduced an innovative approach to better...
Security Essential Series – Penetration Testing vs Vulnerability Scanning
Vulnerability scanning and penetration testing are two fundamental methods used in cyber security to assess and mitigate potential risks in computer systems and networks. Vulnerability scanning involves the use of automated tools to identify known security weaknesses...
Penetration Testing in the NHS DSPT
Penetration Testing in the NHS DSPT The NHS Data Security and Protection Toolkit (DSPT) mandates robust cybersecurity measures to protect sensitive patient data. Distinguishing Penetration Testing from Vulnerability Scanning While both aim to enhance security,...
DTAC, DSPT, and the Importance of Penetration Testing
The DSPT is Evolving: Key Changes and Why They Matter In September 2024, the Data Security and Protection Toolkit (DSPT) will undergo a significant transformation by adopting the National Cyber Security Centre's Cyber Assessment Framework (CAF) as its basis for cyber...
MITRE ATLAS
MITRE ATLAS (Adversarial Threat Landscape for Artificial-Intelligence Systems) is a critical resource for anyone involved in the development, deployment, or security of artificial intelligence (AI) systems. It provides a detailed knowledge base of tactics, techniques,...
LLM AI Security & Governance Checklist
Introduction The rapid rise of powerful generative artificial intelligence (GenAI) applications is poised to impact internet users and businesses significantly. While offering immense potential for discovery, efficiency, and corporate growth across various industries,...
A Comprehensive Guide to LLM Security
Large Language Models (LLMs) have rapidly become essential tools in various sectors, from content generation to decision support. However, their increasing utility and complexity bring forth a slew of security and ethical concerns.
OWASP Top 10 For LLM 2025 (Large Language Model)
The surge in popularity of Large Language Models (LLMs) after the widespread introduction of pre-trained chatbots in late 2022 has been astonishing. Companies, keen to leverage the capabilities of LLMs, are swiftly incorporating them into their systems and customer-oriented services.
Cheat Sheet Series – Web Service Security
Web Service Security (often abbreviated as WS-Security) refers to a suite of protocols and standards that ensure the protection and security of web services. The cheat sheet below condenses insights extracted from the OWASP article about web service security. This...
Cheat Sheet Series – Credential Stuffing
The cheat sheet below condenses insights extracted from the OWASP article about credential stuffing prevention. This table aims to offer a concise and user-friendly overview that can be swiftly referenced for a quick grasp of key points. For further information,...
Cheat Sheet Series – Authentication
The cheat sheet below condenses insights extracted from the OWASP article about security best practices for authentication. This table aims to offer a concise and user-friendly overview that can be swiftly referenced for a quick grasp of key points. For further...
Cheat Sheet Series – Input Validation
The cheat sheet below condenses insights extracted from the OWASP article about user input validation. This table aims to offer a concise and user-friendly overview that can be swiftly referenced for a quick grasp of key points. For further information, please visit...
Motion Picture Association (MPA) and Penetration Testing Requirements
The Motion Picture Association (MPA) supports content creators throughout the production lifecycle by publishing comprehensive Content Security Best Practices on behalf of its member companies: Netflix Studios, LLC; Paramount Pictures Corporation; Sony Pictures...