What is OWASP
The Open Web Application Security Project (OWASP) is a prominent, non-profit international organization dedicated to enhancing the security of web applications. One of OWASP’s foundational beliefs is in making their resources readily available for free on their website. With its vast membership and multiple chapters worldwide, OWASP has established itself as a trusted source for vital web application and API security insights.
Every developer, regardless of their expertise, should invest time in understanding potential code vulnerabilities to prevent problematic and often expensive security mishaps. So, what exactly is the OWASP Top 10?
OWASP updates and releases its list of the top 10 most critical web application vulnerabilities every few years. This list not only outlines the main threats as per OWASP but also delves into the potential consequences of each vulnerability and methods to mitigate them. This extensive list is curated with input from various experts, including security consultants, vendors, and corporate security teams. It stands as a gold standard for best practices in web application security.
In 2021, OWASP introduced a new version of the Top 10, which saw the inclusion of three fresh categories, modifications in the naming and scope of four categories, and certain consolidations.
While the primary objective of the OWASP Top 10 is to foster awareness, since its inception in 2003, businesses have adopted it as an informal benchmark for application security. A closer look at the document reveals references to several associated CWEs (Common Weakness Enumeration).
OWASP Top 10
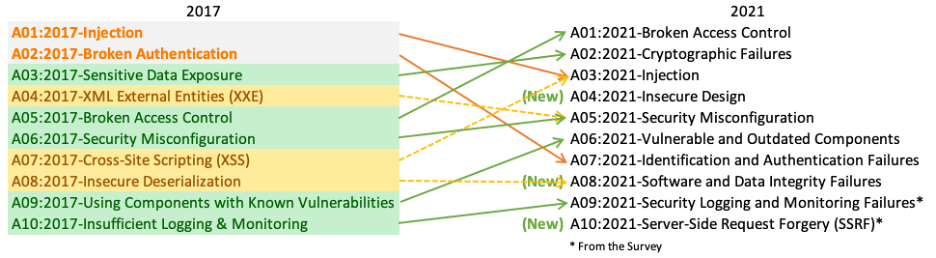
A01:2021-Broken Access Control (Up from #5) This vulnerability reclaims the top spot, appearing in 94% of tested applications and having more occurrences of mapped Common Weakness Enumerations (CWEs) than any other category. It’s the most critical risk.
A02:2021-Cryptographic Failures (Up from #3) Formerly “Sensitive Data Exposure,” this category now specifically targets failures in cryptography that lead to data exposure or system compromise. The focus is on the root cause rather than just the symptom.
A03:2021-Injection (Down from #1) While sliding to third, Injection remains highly prevalent, tested in 94% of applications with the second most mapped CWE occurrences. Cross-site Scripting (XSS) is now included in this category.
A04:2021-Insecure Design (New Category) A new addition emphasizing risks stemming from design flaws. It highlights the industry’s push to “move left” by encouraging practices like threat modeling, secure design patterns, and reference architectures.
A05:2021-Security Misconfiguration (Up from #6) Moving up, this risk affects 90% of tested applications. Its rise is attributed to the increasing complexity and configurability of modern software. The former XML External Entities (XXE) category is now part of this one.
A06:2021-Vulnerable and Outdated Components (Up from #9) Previously “Using Components with Known Vulnerabilities,” this category moved up significantly, validated by both community surveys and data analysis. It represents a persistent challenge in testing and risk assessment, notably being the only category without mapped CVEs, using default exploit/impact scores.
A07:2021-Identification and Authentication Failures (Down from #2) Formerly “Broken Authentication,” this category includes broader identification failures and has dropped in ranking. This improvement is likely due to the increased availability and adoption of standardized authentication frameworks.
A08:2021-Software and Data Integrity Failures (New Category) This new category addresses risks where assumptions are made about software updates, critical data, or CI/CD pipelines without proper integrity verification. It includes Insecure Deserialization from the 2017 list and has some of the highest-weighted impacts from CVE/CVSS data.
A09:2021-Security Logging and Monitoring Failures (Up from #10) Rebranded from “Insufficient Logging & Monitoring,” this category, driven by community survey input, expands to cover more types of logging failures. Though challenging to test for and underrepresented in CVE/CVSS data, it’s crucial for visibility, incident alerting, and forensics.
A10:2021-Server-Side Request Forgery (SSRF) (New Category) Added based on strong community survey support (ranking #1 there), even though data currently shows a relatively low incidence rate. Its inclusion reflects the security community’s belief in its high exploit and impact potential, making it a priority.