SERVICES
What we do
Attack Vector offers a wide range of penetration testing services designed to thoroughly assess your environment and uncover vulnerabilities that could have an adverse impact on your day-to-day business. Our approach and methodology ensure comprehensive coverage and quick turnaround time, allowing you to mitigate issues quicker.
Infrastructure Testing
Learn MoreInternal and External Network Penetration Test
Web Application Testing
Learn MoreWeb application and API assessment
Cloud Security Review
Learn MoreSecurity assessment of AWS, Google Cloud, Microsoft Azure and other cloud providers
NHS DTAC Assessment
Learn MoreAssesment of the technology stack to ensure compliance with the latest NHS technical requirements.
Server & End-User Device Review
Learn MoreSecurity assesments of servers and end-user devices in order to identify security shortcomings and potential escelation of privileges.
Other Services
Learn MoreSee our complete list of technical services.
OUR Advantage
Why choose us
Highly Experienced Consultants
Diverse Industry Experience
Up-to-Date Testing Methodologies
Quick Turnaround
Flexible and Detailed Reporting
Open Communication
We believe that safeguarding your data and your digital assets is of paramount importance. Our mission is to detect and assist in mitigating your organisation’s most critical vulnerabilities, ensuring that you can operate with confidence in an increasingly interconnected world.
With many years of experience in the cybersecurity industry, our team has earned a great reputation for being a trusted partner in the field. Our expertise extends across various industries, enabling us to cater to the unique security challenges that each sector faces. Whether you operate in finance, healthcare, government, technology, or any other line of business, our adaptable approach ensures that we tailor our services to align with your specific requirements.
As a company, we understand that effective cyber security is a collaborative effort. That’s why we work hand in hand with our clients, striving to build a partnership based on trust and transparency.
EXPERTISE
Our partners and accreditations
experience
Proven record
Years Industry Experience
Completed Projects
working with us
Our end to end process
Our scoping process starts with a simple phone call between our cybersecurity consultants and the client. The purpose of the call is to understand the main concerns, reasons for the assessment, and get familiar with your unique requirements.
The purpose of this call is to ensure that everything is set up for the assessment and that there are no technical or business challenges that could cause delays. We also check if the agreed-upon targets from the scoping call are still valid and make sure all required credentials are ready for the assessment. It’s all about making sure everything is in place for a smooth assessment process.
In this main phase of the project, our team delves into the details, discovering valuable information, results, and potential vulnerabilities. Our expert consultants use their technical expertise to conduct a comprehensive assessment. Throughout this process, we maintain open communication with our clients, providing updates through summary emails or end-of-day debrief calls to keep everyone informed.
Our reporting structure is tailored for diverse audiences, catering to the needs of high-level management, technical teams, and stakeholders.
We firmly adhere to the principle of offering personalised, context-specific insights and remediation recommendations, recognising the distinctiveness of each individual environment we assess.
After delivering the report and allowing the client sufficient time to review the valuable information, our consultants schedule a final call to address any queries raised. We are more than willing to provide clarifications on our findings and offer additional guidance if required.
simple process
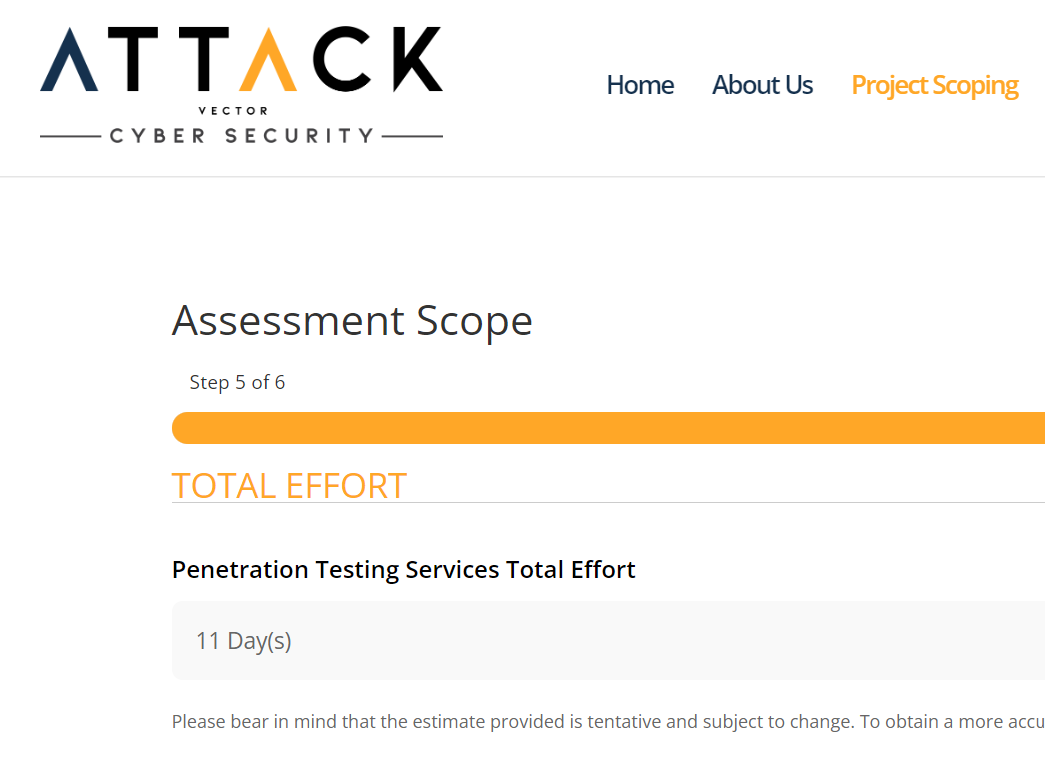
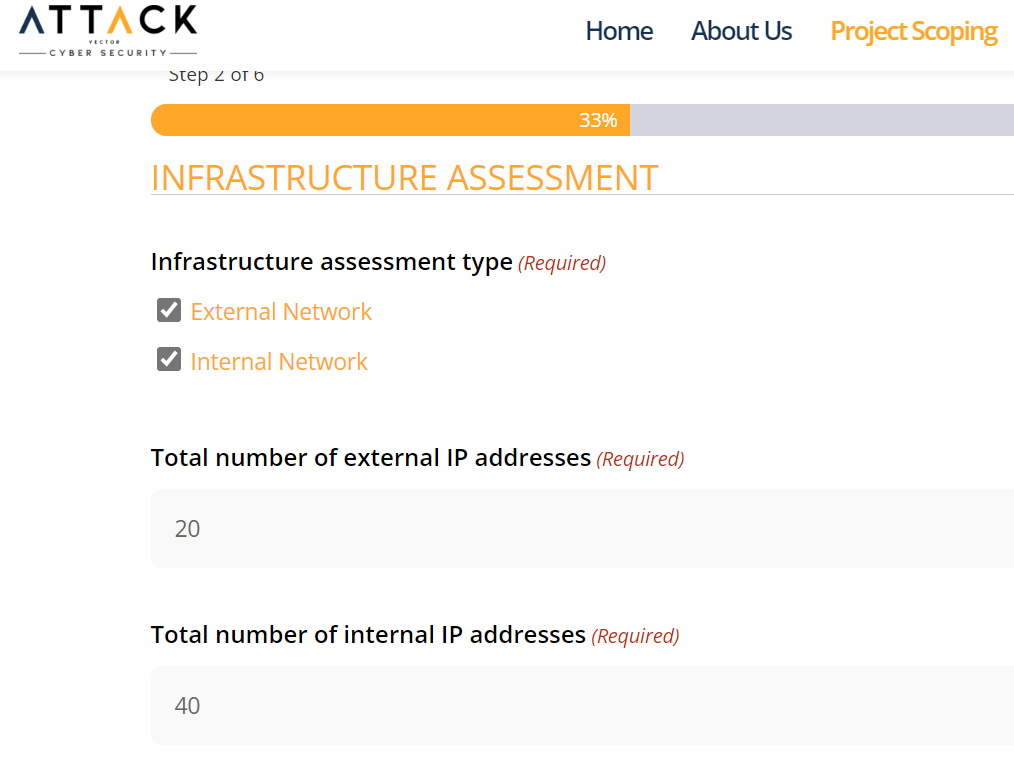
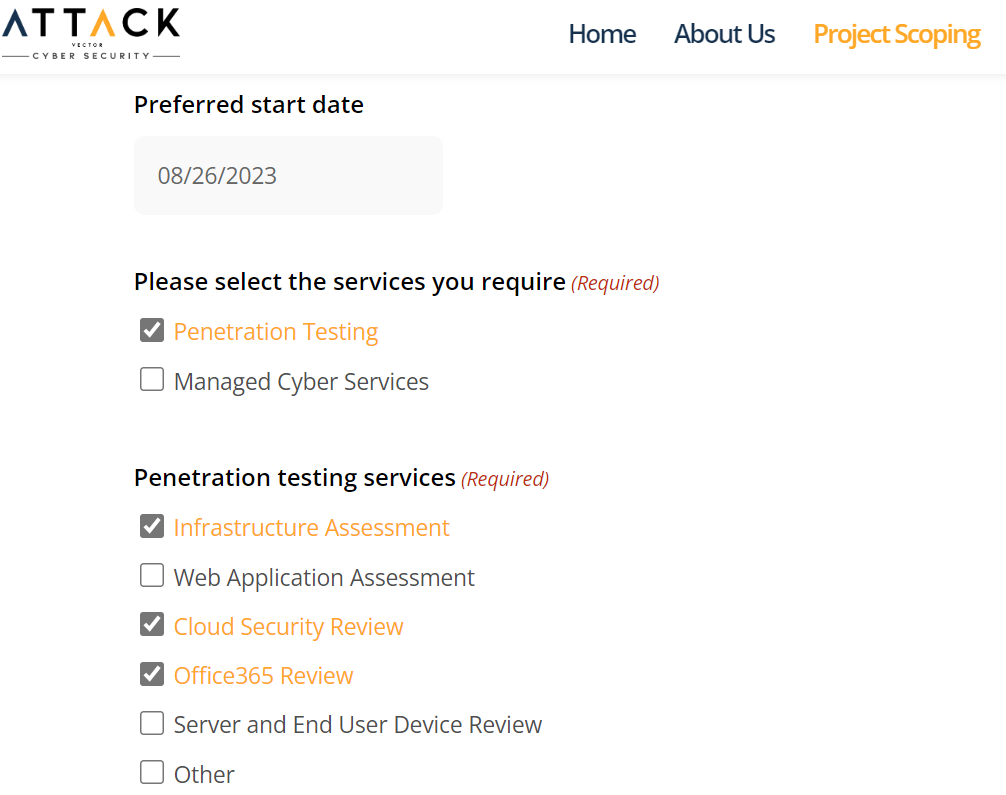
Get instant quotes
If you’re familiar with the process of penetration testing, feel free to utilise our complimentary Effort Estimate & Instant Quote Form. However, if you’re uncertain about where to begin (or prefer direct consultation with an expert), kindly reach out to us through our CONTACT page. We’ll arrange a call to walk you through the process.
Get quotes instantly and see them right in the scoping form. No need to sign up before getting your quote – we’re all about being upfront and transparent.